ATWINC1500 IoT Module Deep-Dive (Part 1)¶
This is the second article in the Hunter Hacking Project series.
The Microchip ATWINC1500 IoT Module is a low-cost 802.11 b/g/n WiFi module, popular in the "maker" DIY electronics communities,
- Adafruit Feather M0 WiFi
- Adafruit ATWINC1500 WiFi Breakout
- Arduino WiFi Shield
- Arduino WiFi101 Library
Support for the module is even baked into Arduino: WiFi101 / WiFiNINA Firmware Updater
History¶
Originally designed by Newport Media Inc., along with the WILC1000/WILC3000 family of WiFi modules, the ATWINC1500 module became part of Atmel's SmartConnect family through the acquisition of Newport Media in 2014.
Two years later, the device changed owners once again and became part of Microchip's portfolio through Microchip's acquisition of Atmel in 2016.
This is useful to know because the ATWINC1500 codebase bears the hallmarks of this tumultuous history.
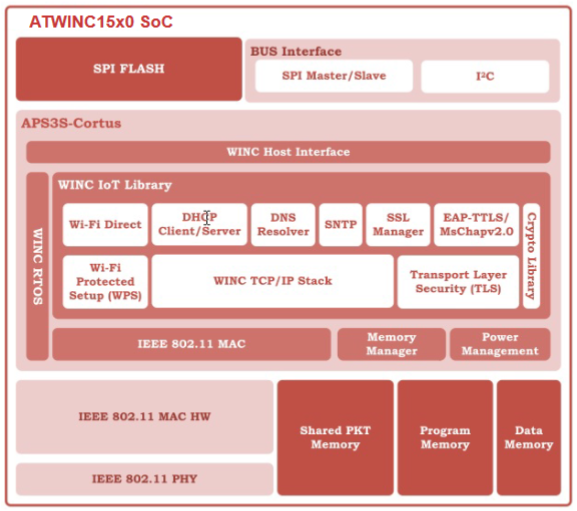
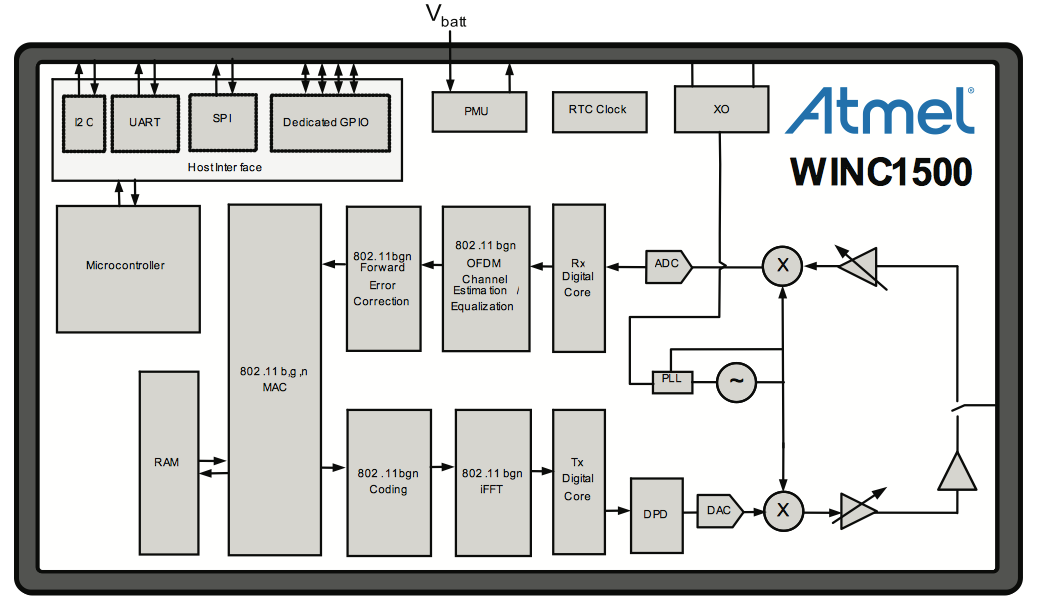
Architecture¶
The module has an embedded Cortus APS3S 32-bit RISC processor with either 2Mb or 4Mb of internal SPI flash.
The Wi-Fi Network Controller Software Design Guide provides this system architecture diagram:
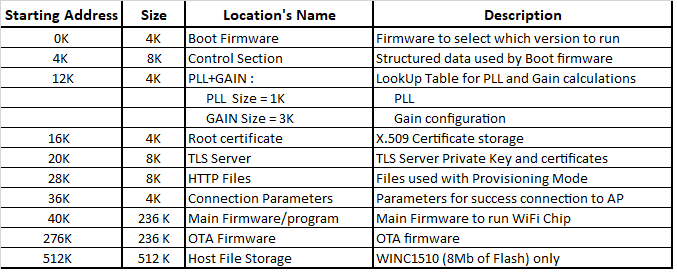
Memory Map¶
Root Certificate and TLS Certificate in ATWINC15x0 provides the following memory map:
(the table above is extracted from spi_flash_map.h)
What immediately stands out are the two regions "Root certificate" and "TLS Server".
Why?
Well, because trusted root certs are distributed as X.509 certs and private keys are always highly prized. Don't know what that means? We'll get to it.
Microchip elaborates:
Why is there two location to store certificates in ATWINC15x0 flash? What is the difference between Root Certificate and TLS Certificate/key storage in ATWINC15x0 flash memory?
There are two specific locations to store different certificates into WINC flash memory:
X.509 Root Certificate storage - This is for the ATWINC1500 TLS Client to verify the TLS server certificate (A self signed public key certificate that identify the authority) from the server that the module is trying to connect. (eg. When ATWINC1500 is trying to connect to google.com, device will use the "GlobalSign Root CA" certificate stored in the Root Certificate folder to verify the server certificate)
ATWINC1500 TLS Server certificate storage - For proper operation of both the TLS server and TLS client authentication, the ATWINC1500 device must have a certificate/private key pair assigned to it.
Let's see what else we can find.
A Quick Primer On TLS¶
Well versed in TLS? skip this section
Transport Layer Security (TLS) is a cryptographic protocol used to secure communication over the internet. It is widely used to provide secure communication for web traffic, email, and other applications that require secure communication. TLS uses a combination of symmetric and asymmetric encryption to provide confidentiality, integrity, and authenticity of the data exchanged between two parties.
One of the key components of TLS is the X.509 digital certificate, which is used to verify the identity of the communicating parties. X.509 certificates contain information such as the name of the entity being identified, the entity's public key, the digital signature of the certificate issuer (Certificate Authority) which signed the certificate, and the validity period of the certificate.
To use TLS, both parties need to have a pair of private and public keys. The private key is kept secret by the owner and is used to encrypt and decrypt data. The public key, on the other hand, is freely distributed and is used to encrypt data that can only be decrypted by the corresponding private key.
Info
The ATWINC1500 stores these private and public keys in the TLS Cert Store.
When a client initiates a TLS connection with a server, the server sends its X.509 certificate to the client. The client then verifies the authenticity of the certificate by checking the digital signature of the certificate issuer (Certificate Authority). If the certificate is valid, the client can use the public key in the certificate to encrypt data that can only be decrypted by the server's private key.
Certificate Authorities (CA) are trusted third-party entities that issue X.509 certificates. A CA verifies the identity of an entity and signs its certificate to provide a chain of trust. This chain of trust can be traced back to a Root CA, which is trusted by default in most operating systems and web browsers.
Info
The ATWINC1500 stores the trusted Root CA certificates in the Root Cert Store. If a server returns a certificate signed by a certificate stored in the Root Cert Store, the ATWINC1500 will assume it can trust it, and will allow the connection.
Finally, TLS uses Abstract Syntax Notation One (ASN.1) to encode data in a compact and efficient format. ASN.1 is a standard that defines a notation for describing data structures that can be encoded and decoded in a machine-independent way. TLS uses ASN.1 to encode and transmit X.509 certificates, keys, and other cryptographic parameters in a compact format that can be easily decoded by the receiving party.
To summarize: 1. X.509 is a standard defining the file format of certificates. 2. A certificate is basically a public key which has been signed by someone else's private key. 3. "Someone else" is a usually a "Certificate Authority", but certificates can also be self-signed. 4. Certificates also bundle identity data (common name, address, etc.) along with the public key, and the kaboodle is signed by the CA. 5. TLS private and public keys are stored in a format called ASN.1, which is translated into PEM, DER, CER, and other formats, as needed.
Need more detail?
Section 7 of the Wi-Fi Network Controller Software Design Guide contains a wealth of additional information.
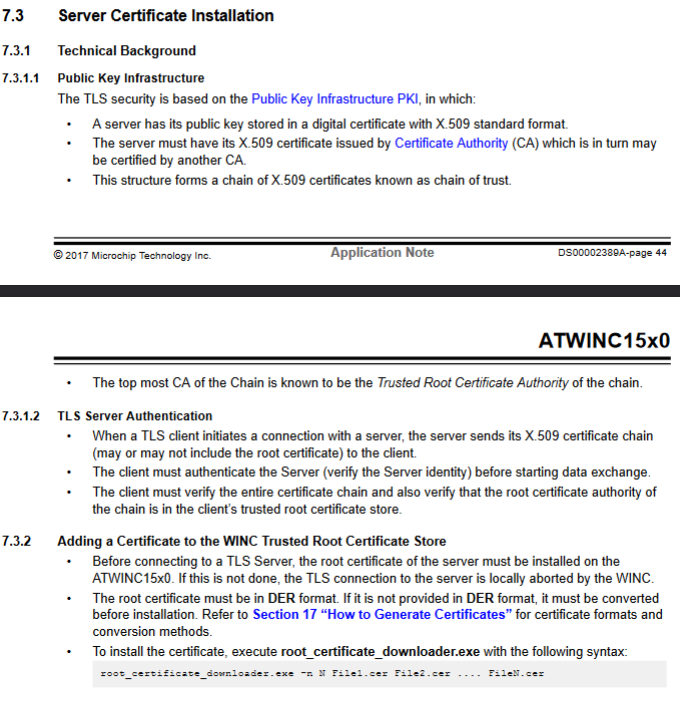
Root Certificate Store¶
The Wi-Fi Network Controller Software Design Guide explains that:
Before connecting to a TLS Server, the root certificate of the server must be installed on the ATWINC15x0...
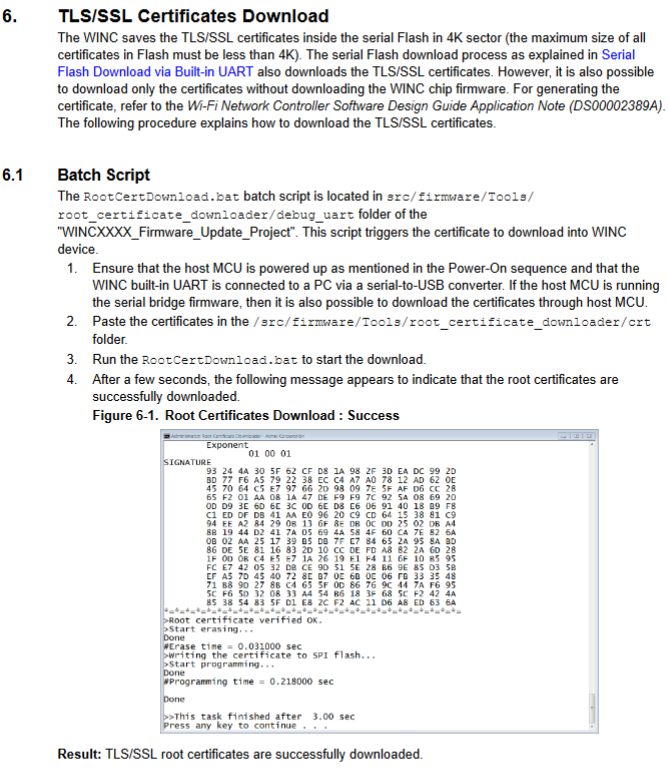
And Integrated Serial Flash and Memory Download Procedure describes the procedure for installing certificates:
TLS Server Store¶
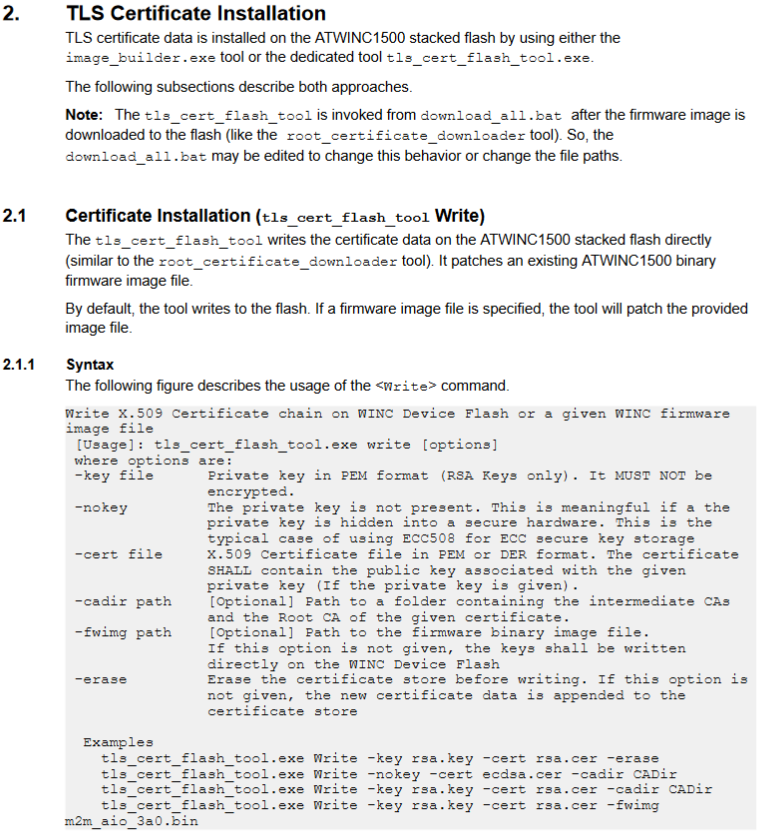
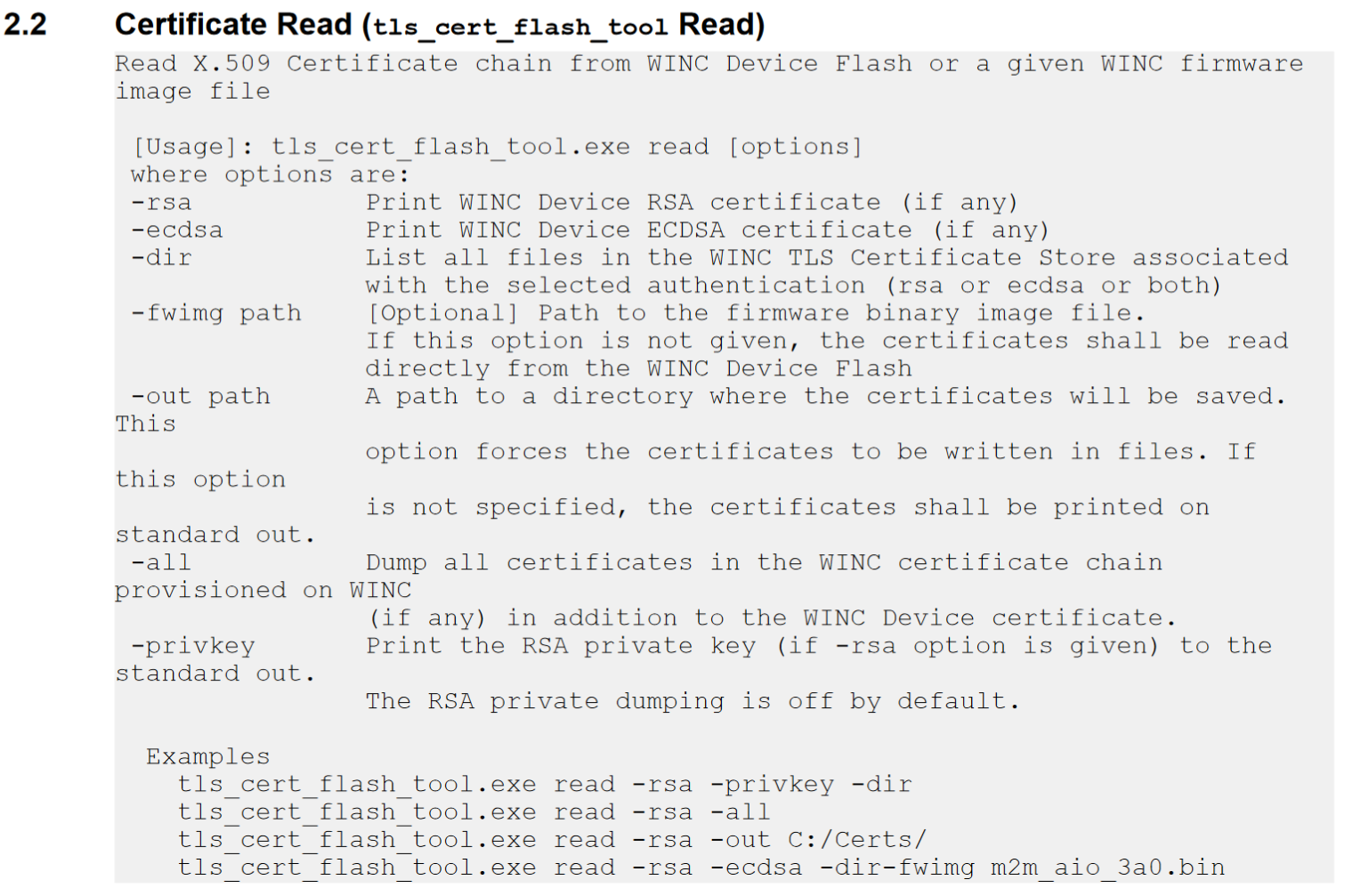
The Transport Layer Security (TLS) User's Guide describes the procedure for installing certificates:
Interfaces¶
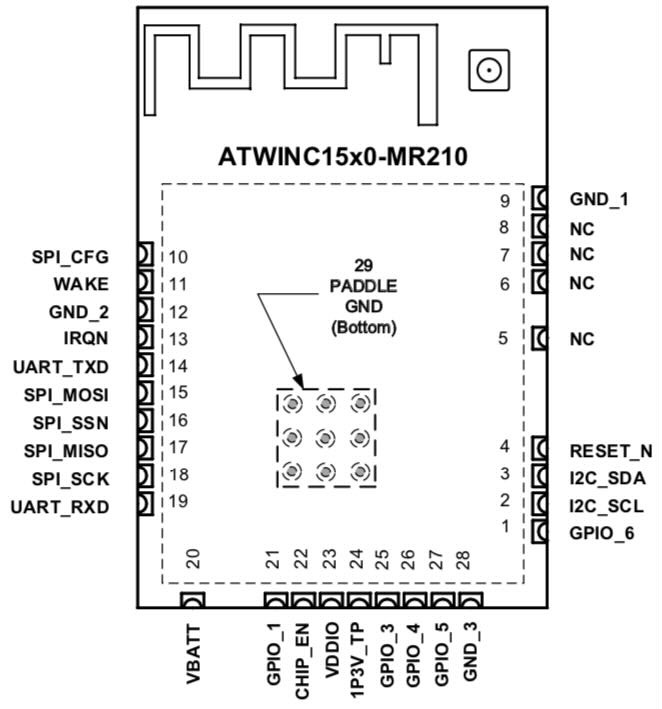
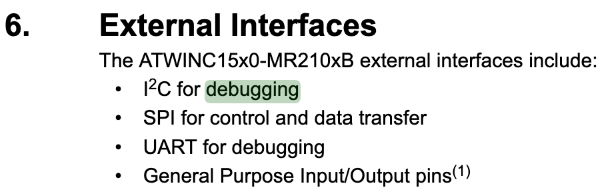
Page 7 of the datasheet contains a pin-out diagram which indicates that the module has the following interfaces: UART, SPI, and I2C.
The datasheet explains that the SPI interface is used to communicate with a host microcontroller.
Debug Interfaces¶
Page 20 of the datasheet indicates that the UART and I2C interfaces are for "debugging purposes" only:
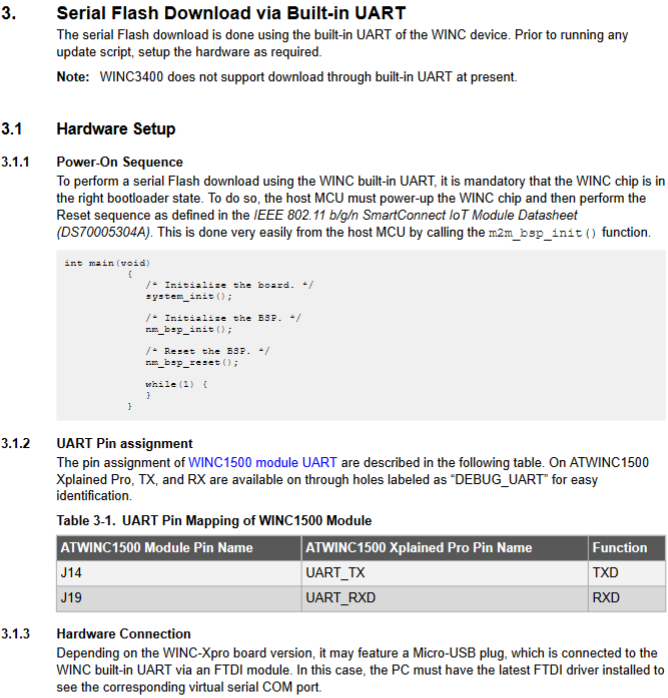
Debug UART¶
Integrated Serial Flash and Memory Download Procedure explains that to perform a serial flash download, the chip needs to be in the right "bootloader state":
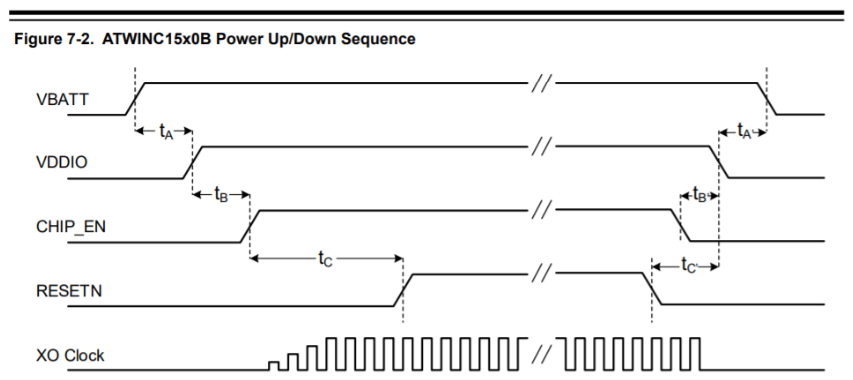
The online documentation provides this handy diagram which explains what m2m_bsp_init() is doing behind the scenes:
Firmware Extraction¶
The WINC1500: Using Image Tool to build firmware image, gain table and program using serial bridge mentions that the module's firmware can be extracted by connecting a 3.3v TTL USB-to-Serial cable to pins UART_TXD and UART_RXD of module and executing the following command:
winc_programmer_uart.exe -p COM4 -d winc1500 -r -pfw programmer_firmware.bin -o atwinc1500-original.bin
Let's give it a shot!
Alternatively, you can use the Microchip image_cloner.exe tool
You can download a compiled binary: here
Hardware Setup¶
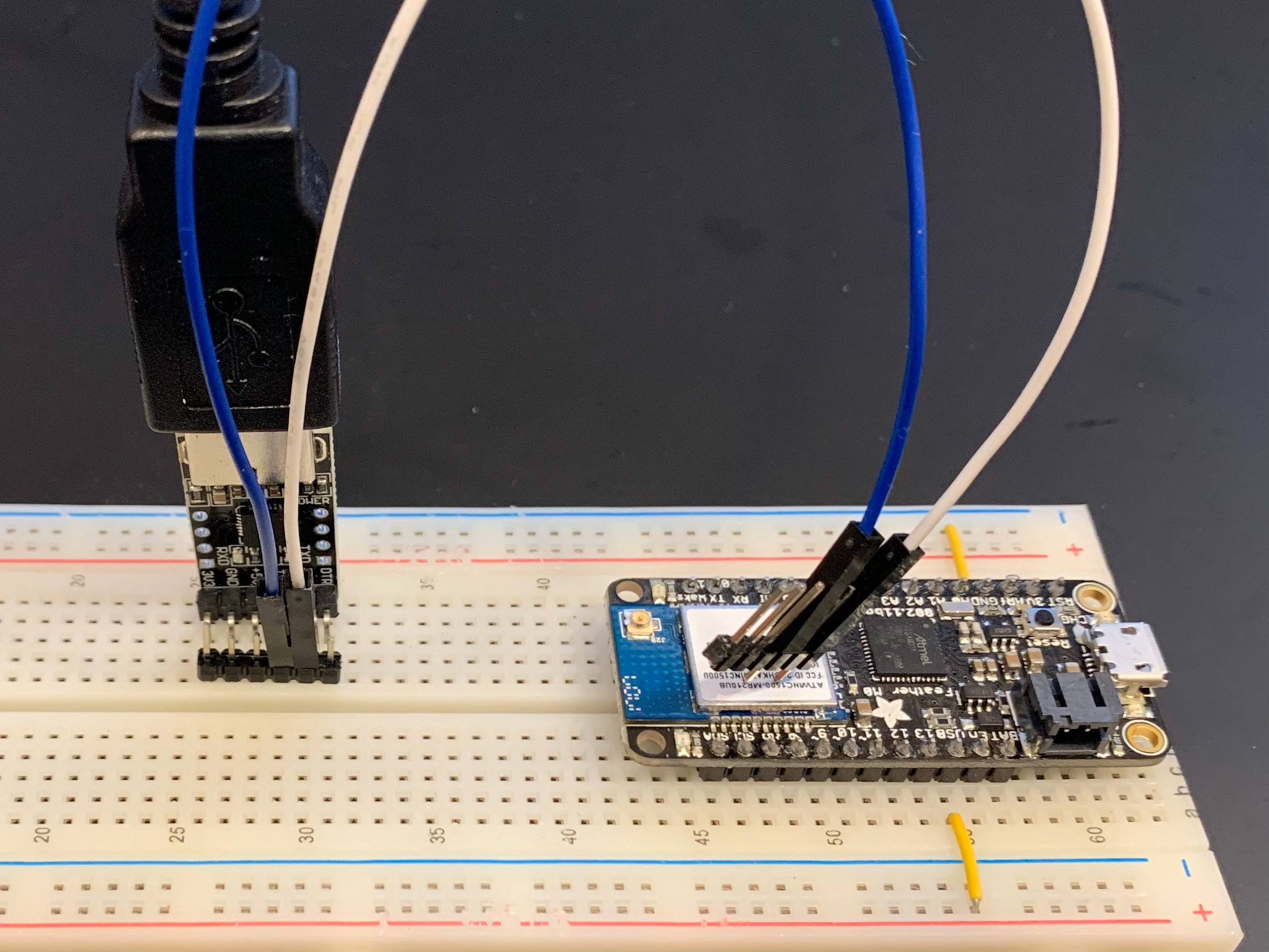
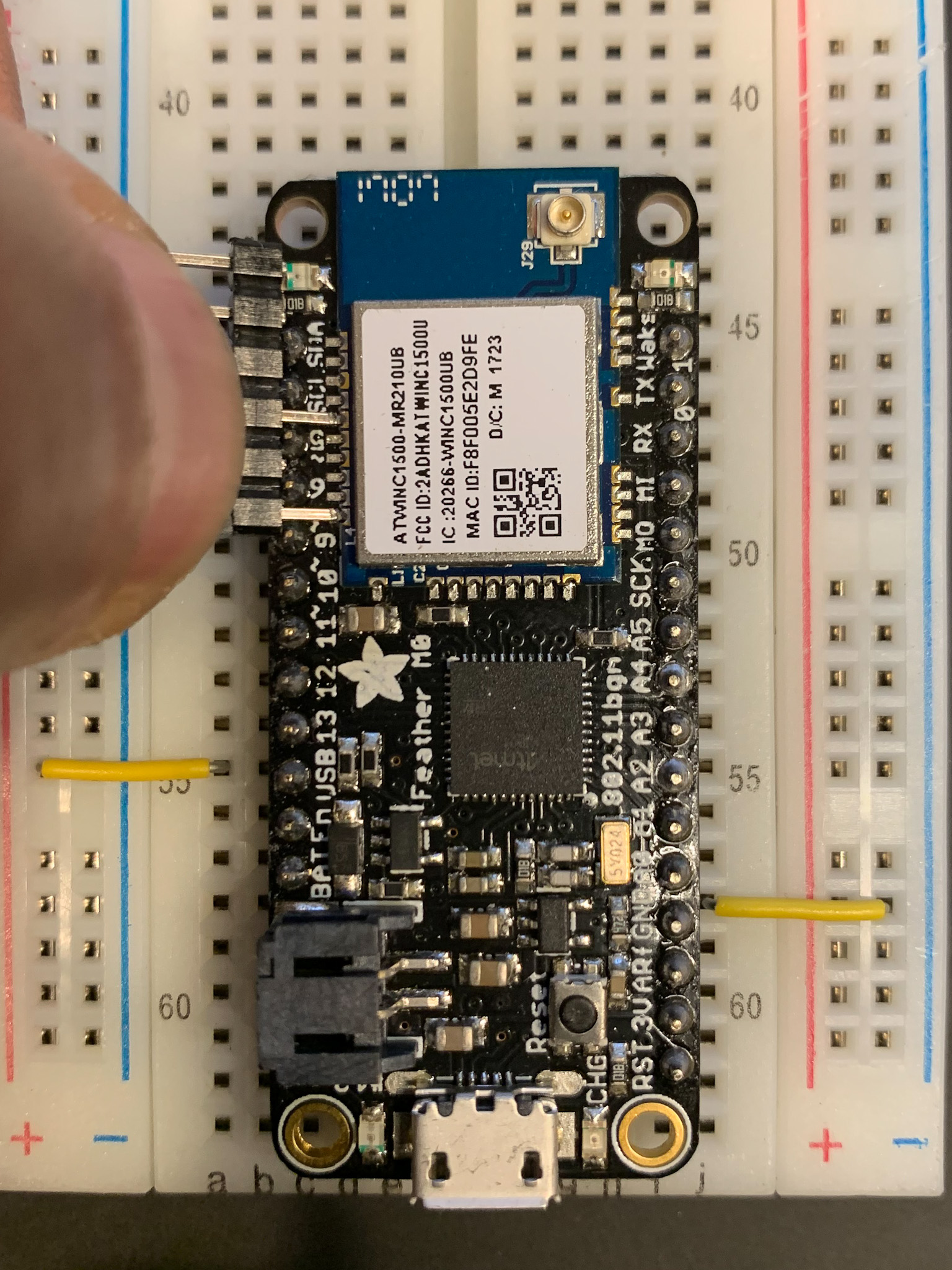
I will be using the above method to extract firmware from an Adafruit Feather M0 WiFi development module using a cheapo CP2102 USB-TTL UART module:
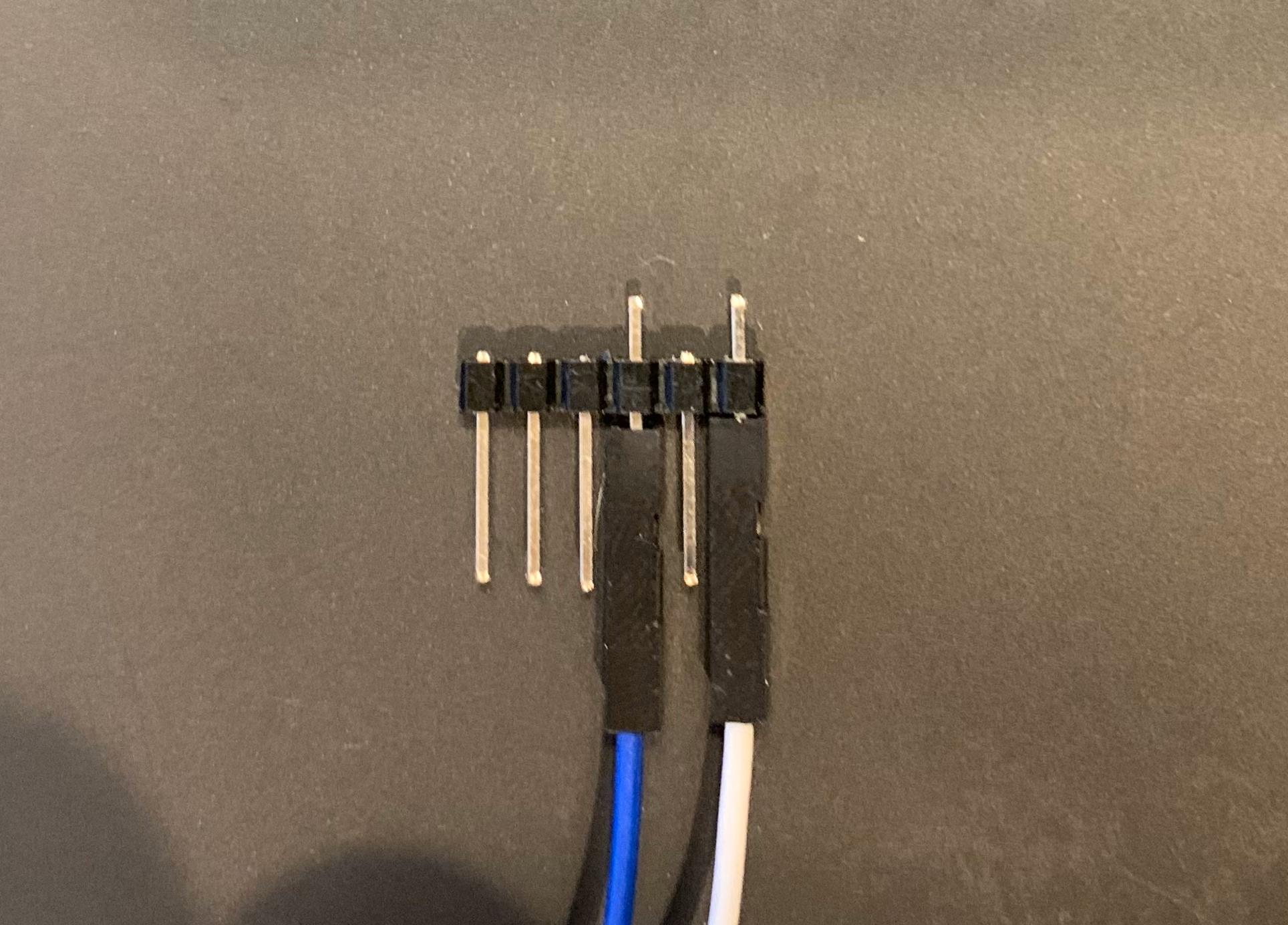
Since I don't have a fancy POGO rig, I made a simple jig to hold the leads in place while the firmware is extracting:
Software Setup¶
As mentioned in ATWINC1500 IoT Module Deep-Dive (Part 1)#Debug Interfaces, to enable the debug interfaces, the ATWINC1500 module needs a specific boot-up sequence.
Since the Adafruit Feather M0 is supported by Arduino, I wrote a simple sketch:
#define CE_PIN 2
#define RST_PIN 4
void setup() {
pinMode(LED_BUILTIN, OUTPUT);
pinMode(CE_PIN, OUTPUT);
pinMode(RST_PIN, OUTPUT);
digitalWrite(CE_PIN, LOW);
digitalWrite(RST_PIN, LOW);
delay(1000);
digitalWrite(CE_PIN, HIGH);
delay(100);
digitalWrite(RST_PIN, HIGH);
}
void loop() {
digitalWrite(LED_BUILTIN, HIGH); // turn the LED on (HIGH is the voltage level)
delay(1000); // wait for a second
digitalWrite(LED_BUILTIN, LOW); // turn the LED off by making the voltage LOW
delay(1000);
}
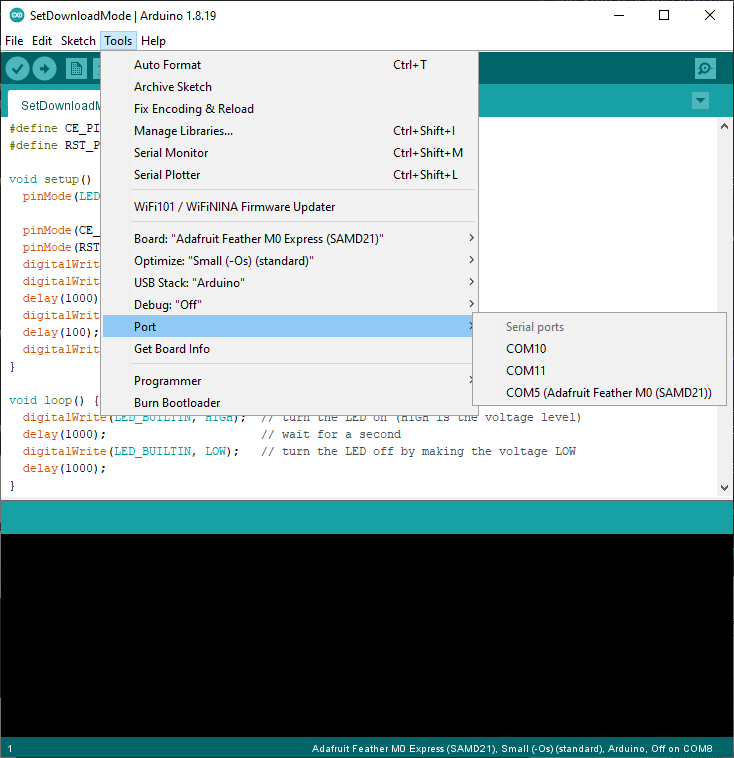
Don't forget to set the Port!
The bossac programmer will silently fail if you forget to set the port.
Executing Dump¶
Adafruit Feather M0 Firmware Dump
$ winc_programmer_uart.exe -p COM4 -d winc1500 -r -pfw programmer_firmware.bin -o atwinc1500-adafruit.bin
WINC Programming Tool 2.0.1 [ceebe5f] (Apr 20 2022)
Copyright (C) Microchip Technology Inc. 2022
hardware WINC serial bridge found
chip ID is 0x001503a0
programming firmware file: programmer_firmware.bin
reinitialise onchip uart to 500000
waiting for firmware to run
flash ID 0xc21320c2
flash size is 4 Mb
begin read operation
0x000000:[rrrrrrrr] 0x008000:[rrrrrrrr] 0x010000:[rrrrrrrr] 0x018000:[rrrrrrrr]
0x020000:[rrrrrrrr] 0x028000:[rrrrrrrr] 0x030000:[rrrrrrrr] 0x038000:[rrrrrrrr]
0x040000:[rrrrrrrr] 0x048000:[rrrrrrrr] 0x050000:[rrrrrrrr] 0x058000:[rrrrrrrr]
0x060000:[rrrrrrrr] 0x068000:[rrrrrrrr] 0x070000:[rrrrrrrr] 0x078000:[rrrrrrrr]
output file format not specified, assuming 'raw'
If you're using an older version of winc_programmer_uart.exe you might get the following error
$ winc_programmer_uart.exe -p COM4 -d winc1500 -r -pfw programmer_firmware.bin -o atwinc1500-adafruit.bin
WINC Programming Tool 1.0.3 [r708] (Jul 28 2020)
Copyright (C) Microchip Technology Inc. 2020
hardware WINC serial bridge found
chip ID is 0x001503a0
programming firmware file: ..\programmer_firmware\release3A0\programmer_firmware.bin
reinitialise onchip uart to 500000
waiting for firmware to runerror(uart_read:61): incomplete read from UART
error: failed to receive read register response
error: failed to initialise programming firmware '..\programmer_firmware\release3A0\programmer_firmware.bin' on device
Firmware Analysis¶
Now that we've got a fresh binary sitting in atwinc1500-adafruit.bin, let's see what's inside.
Using the tls_cert_flash_tool.exe mentioned in TLS Server Store we can investigate the TLS Store.
TLS Server Store Summary¶
Due to a bug, the tool reports the "WINCRootCA" twice, so there are only 4 certs stored in the TLS Store:
```bash hl_lines="" $ tls_cert_flash_tool.exe read -fwimg atwinc1500-adafruit.bin -ecdsa -rsa -dir
- WINC1500 TLS Certificate Flash Tool *
PRIV_00ddb578c5a531f273 1208 PRIVATE KEY CERT_00ddb578c5a531f273 950 CERTIFICATE *.winc.atmel.com CERT_00def74d6dfa50e85c 1003 CERTIFICATE WINCRootCA
CERT_00f4bb2e4a6fd5ae51 579 CERTIFICATE *.winc.atmel.com CERT_00ddefc26b1df1c50d 754 CERTIFICATE AtmelEccCA CERT_00def74d6dfa50e85c 1003 CERTIFICATE WINCRootCA
== X509 == Subject <*.winc.atmel.com> Issuer
== X509 == Subject <*.winc.atmel.com> Issuer ---
### Dumping TLS Private Key
```bash
$ tls_cert_flash_tool.exe read -fwimg atwinc1500-adafruit.bin -rsa -privkey
******************************************
* WINC1500 TLS Certificate Flash Tool *
******************************************
Private-Key: (2048 bit)
modulus (N):
AD 62 49 6E 87 72 FA D4 E0 1A 48 1C B8 B4 5E D1
9D B9 EC A4 99 86 6D 23 9E 10 BD 8D D3 07 FA 58
63 D1 E9 FB 8D A5 9B 61 83 68 4D 17 C8 35 E1 85
89 85 6F 29 91 CC AC A4 B1 3C E2 F4 E3 81 9E 30
8A 86 11 FF D4 97 C0 DD B1 14 64 44 14 C9 F9 BA
59 1B 8F 82 07 23 D0 00 C1 AD 95 BC 28 39 19 87
FB F3 10 5E 25 EF FB 8A 54 CA 96 1F A2 03 1C 90
DB 51 44 93 C9 11 EF 3F 93 34 66 36 6B 48 44 61
14 0A FE 15 AB 53 74 0B F7 30 F8 7B 3E 55 98 32
10 94 53 FA BC C4 C2 0D CE 91 F5 3D 50 3B 69 A8
3A AF 03 09 C4 A4 74 4C 62 49 98 C9 FC 1E 9B 7F
A7 9B 2D A4 BF C2 AE 42 D0 E7 09 27 D2 E4 CD DC
D0 88 3B 43 20 F2 15 0D 32 92 8E 4D 9E C6 E9 C6
DE 7D 65 01 22 E1 B7 60 6F C0 27 11 7C F7 FA FD
7C FE 5B 23 A7 00 56 DF 99 ED 1A 44 CF D6 BA F9
8A 09 6A D3 54 81 55 25 86 7D C0 7C 68 CC FF 31
publicExponent (e):
01 00 01
privateExponent (d):
3D 37 5D 9B E3 C0 E9 E4 ED 36 FA 4D 01 BD D5 58
87 2A D4 ED 8C B3 14 A7 A5 B0 5D 6C CC 9C 9D 7C
45 CA 20 A5 CB 6E 34 3D 2A AB 51 C4 DA D0 83 4E
A5 AE 72 00 28 55 2E 83 7B 7C 76 D9 65 D6 26 E7
16 91 9D 9B 49 11 47 6C 3E 90 67 92 4E 10 BD D6
58 8D CD 8E 68 3C F1 BC C2 A5 2A 1F E3 C7 BD 46
F0 E2 F1 DD 7B E1 8E 5B 59 F2 A9 2C 84 04 3B 3A
BD E4 A4 A4 D5 32 3A D9 A4 7C B4 B5 F4 0C F0 EF
0C 86 C6 B1 6C EA 63 D5 79 D5 20 37 C0 8E AF 0E
20 E9 6B 91 D4 FB 15 B8 FF E4 1E 80 20 52 3A 7F
C2 83 92 22 AF AC 16 9D 93 0D E6 56 3A 84 E8 B6
77 56 77 AF 23 E3 68 DC 91 14 C8 FC 61 47 57 8C
7D B6 DA 19 13 2A D2 DE D7 E5 BD 59 70 86 AF 39
AD CB 29 75 20 CB 36 93 D3 57 34 74 E0 26 B4 B7
9B 37 49 F8 0E 11 FF 42 72 9B 93 5B 78 BA A8 55
4B 5F 78 E9 99 DE ED 9C 49 28 FC AC 9B B4 E4 C1
prim1 (p):
E1 C9 49 53 EB 34 15 5B 0D E5 01 38 49 4E 0B 40
00 C6 AF 4C C1 EB 59 ED 07 69 5D 40 D7 82 14 21
3E 39 9F 94 F1 B8 FB EA B9 91 FB 7C F0 0D 96 F4
F5 30 81 D5 65 4D 7C 5A 19 35 C4 2D 04 C3 22 F1
73 12 4F 68 97 7A 66 71 D7 68 E5 22 41 B3 AF C4
C4 46 49 40 D5 7A FC EC F4 8D 02 EE 95 C4 01 F2
C5 E7 13 DD 62 D3 FF 46 18 BA 05 24 5C D7 3E 1C
C7 7B 84 66 D8 DC 0C 10 AE FD 8B 53 FF AE 51 19
prime2 (q):
C4 95 DD 3F 4D E1 D3 75 1D CC 3C 82 82 40 4C C7
66 A5 71 A9 A5 DE F1 1A ED FA B5 6F 4A 92 E9 8C
05 1B 4A 67 D3 8A B7 53 6C 83 DD A5 31 34 92 D0
AF 3D FF 06 00 45 C4 A8 12 DF E1 29 8E 93 09 B9
99 25 12 1F 94 F1 09 B8 14 67 9D 35 2A D2 AF 39
05 92 88 F4 DC D3 5E 55 DA 99 C2 0E 8F C2 DC 3D
6B 98 22 40 80 72 6D 1F D9 E2 87 6F 60 33 16 6A
08 B3 2E 61 63 7C EE 69 BF 06 71 9D 1A DF 69 D9
exponent1 (dP):
12 0E 5F CF D7 3A 66 0E CF 10 A6 45 53 0F 6B B4
E5 9A FD FF DC 6E 2E D5 D6 C6 E5 4F 3F 2C C6 E1
55 B1 94 02 7C 46 37 D7 30 99 ED 0B B3 C2 D2 74
AA 7B 03 97 06 2F E9 26 E7 67 36 56 07 50 77 A5
E9 76 E8 64 CB E0 5C FA F3 A8 0E D2 EB 80 2C 29
47 2C FB C4 B4 8D CE 56 40 C4 5A 1C AC 5B 6D 70
75 C5 22 00 8D 5B B8 C9 69 46 CF 0C 76 64 3C 32
5E FD 90 BC 0C D1 A4 21 5D 6D 27 4C 43 61 34 59
exponent2 (dQ):
4F 8B 2C 48 EF 24 8F 41 76 5B 2B A8 CB 37 65 59
D1 C8 E3 E2 F7 40 EC 62 2F 25 20 C0 F5 75 D8 96
55 82 A3 6A BB 88 07 81 F4 08 AF 68 A6 2E 55 B1
A7 16 F8 D7 DE C8 5C 38 7D DA A4 EB 01 CB B1 45
AE 17 F7 EB 5B 82 E4 A1 DD 6F C7 86 B9 DB 22 17
7A 8F BE 67 05 EB 68 E2 68 5F 8A CC 05 93 9D 36
25 11 1B DA E9 9E 63 55 5D FE 71 3A B9 BC 32 37
99 69 97 3C C4 DA CA 45 73 8C 11 F0 B5 EC EC 91
coefficient(QInv):
62 4F E3 8A 73 BD 03 DC 17 DD 17 87 DB 1C EA 88
5E C2 F7 7D 3F 1F 47 52 B2 F5 43 92 A8 D0 9D D0
3E 7E 98 A3 B1 DC 84 90 01 B1 16 D6 0D 05 77 03
EA 0D 10 68 DC 74 D7 82 90 05 7C 80 26 8D C3 2D
7D 96 65 4C 29 6B 1A A2 F7 59 24 40 58 12 77 19
6C 37 FD 94 23 A9 C4 D3 82 67 F4 13 33 09 29 B0
88 D2 80 CC A5 3F C5 E7 53 A6 EA 87 26 0A 42 0E
35 97 07 88 66 4C BA 1A B1 08 92 97 49 74 3C D0
*=*=* X509 *=*=*
Subject <*.winc.atmel.com>
Issuer <WINCRootCA>
<2016-06-12 12:29:03> to <2021-12-03 12:29:03>
Dumping TLS Certificates¶
Unfortunately, the tool only dumps the certificates and not the private key.
# Extract TLS Certificate(s)
tls_cert_flash_tool.exe read -fwimg atwinc1500-adafruit.bin -ecdsa -rsa -all -out output
******************************************
* WINC1500 TLS Certificate Flash Tool *
******************************************
Press any key to continue . . .
$ ls output
AtmelEccCA.cer ECDSA_winc.atmel.com.cer RSA_winc.atmel.com.cer WINCRootCA.cer
Firmware Versions¶
Before we wrap, let's talk about how to upgrade the firmware on our ATWINC1500 module.
As vulnerabilities are found and patched, Microchip, and integrators will roll out firmware updates, I believe the latest firmware (as of March 22, 2023) is 19.7.7, available here.
Checking Firmware Version¶
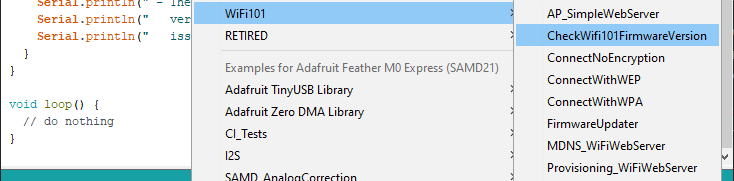
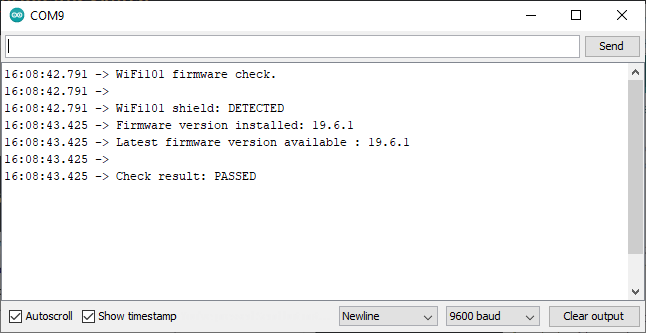
The easiest way I've found to check the ATWINC1500 firmware version is to use the Arduino CheckWifi101FirmwareVersion sketch:
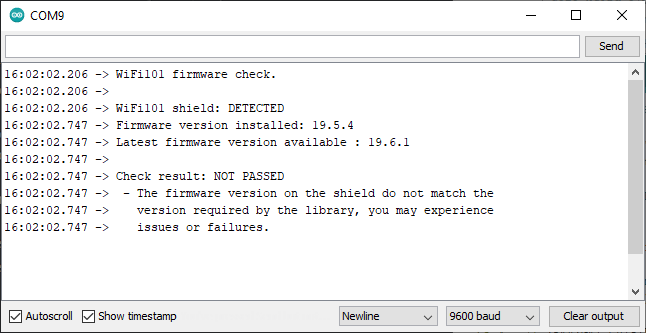
After uploading the sketch to your board it spits out the firmware version:
Updating Firmware¶
The easiest way I've found to upgrade the ATWINC1500 firmware is to use the Arduino "WiFi101 / WiFiNINA Firmware Updater" tool, built right into the Arduino IDE:
Write FirmwareUpdater Sketch¶
To use the updater, you'll need to first upload the FirmwareUpdater sketch
Update Firmware¶
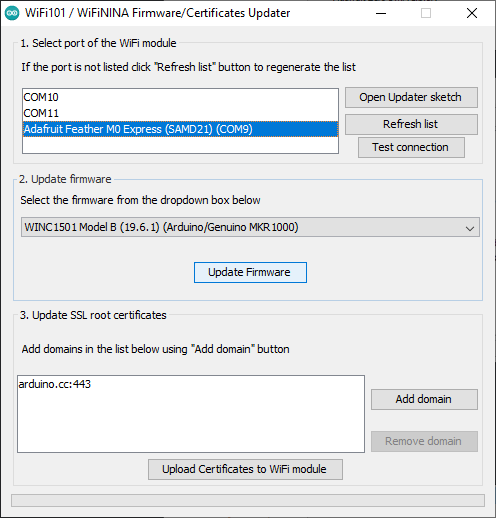
Once the FirmwareUpdater sketch has been uploaded, you can select the board and desired firmware version and click 'Update Firmware':
Resulting in:
Subsequently, running the CheckWifi101FirmwareVersion sketch should result in:
Further Reading¶
Uploading SSL Root Certificates¶
If you're in a hurry, the Arduino "WiFi101 / WiFiNINA Firmware Updater" also provides a convenient way to add certificates to the Root Cert Store.
For example, to add the root cert for www.google.com:
Next Steps¶
Unfortunately, tls_cert_flash_tool.exe is the only tool Microchip provides for extracting information from a firmware binary.
To probe further we're going to have to put on our big boy pants and go down an ADHD hyperfocus rabbit hole.
Follow along in ATWINC1500 IoT Module Deep-Dive (Part 2).